What is Two-factor Authentication (2FA)? #
Two-factor authentication (2FA) is a security method that helps protect company data, business and personal accounts by adding an extra layer of security to just a user name and password.
Commonly used for online transactions, banking and accessing company databases, 2FA uses two forms of authentication — a password and a security code or request (sometimes referred to as ‘security information’) sent to a nominated contact method/device, such as a text message, phone call or push notification via an app.
This makes it more difficult for someone malicious to sign into a bank account, make a fraudulent transaction or access company data as, although they may have obtained a password, it is unlikely they have access to the 2FA security information method or device.
Some services can nominate trusted devices so that 2FA is only needed at set up time and will not be prompted again when accessing sensitive information in corporate-used applications, such as Microsoft Teams or Outlook, or making payments online to a retailer via an online payment method, such as PayPal.
Untrusted devices require the entry of a security code sent to your nominated contact method or via the use of an authentication application every time you sign into the company application.
Some services, such as accessing bank accounts, tend to use this method by default, as an added measure of security.
Types of 2FA #
2FA via text message #
The most common method is to send a one-time password or PIN code via a text message to a mobile number that was set up as the 2FA device. Once received, the recipient can then enter that into a website or application when prompted during the sign-in stage. Quite often, the verification code is typically only valid for a short period of time, maybe 5-20 minutes. Once expired, a new code will need to be requested.
Voice-based authentication #
This method automatically calls the telephone number that has been provided during the sign-up process or in a company profile. When answered, the recipient simply states their name or presses a particular key when prompted to verify the authentication request. If the call is not answered or goes to voicemail, the call is reattempted. If this happens twice, the authentication call is terminated.
Push notifications #
Websites and apps are now able to send push notifications, clickable pop-up messages that appear on a browser or mobile device, informing the person that an authentication is taking place. The recipient simply views the notification and can either approve/deny or accept/decline the request to approve identity. Requiring no passwords or codes, push notifications eliminate any opportunity for phishing, man-in-the-middle attacks, or unauthorised access.
Hardware tokens #
Hardware tokens are one of the oldest forms of 2FA, but are less widely used these days. They are usually provided by businesses in the form of a key fob that can produce one-time passwords or codes every 30 seconds. When a user tries to access an account, database or website a 2FA code is displayed on the fob which must be entered into the relevant field.
Biometric 2FA #
Biometric authentication is another method that could be incorporated into a 2FA solution or as part of a wider multi-factor authentication process. This method uses fingerprints (commonly used by apps on mobile devices, such as banking apps, National Lottery, Google Play Store etc.), facial recognition or retinal scans to verify a person’s identity.
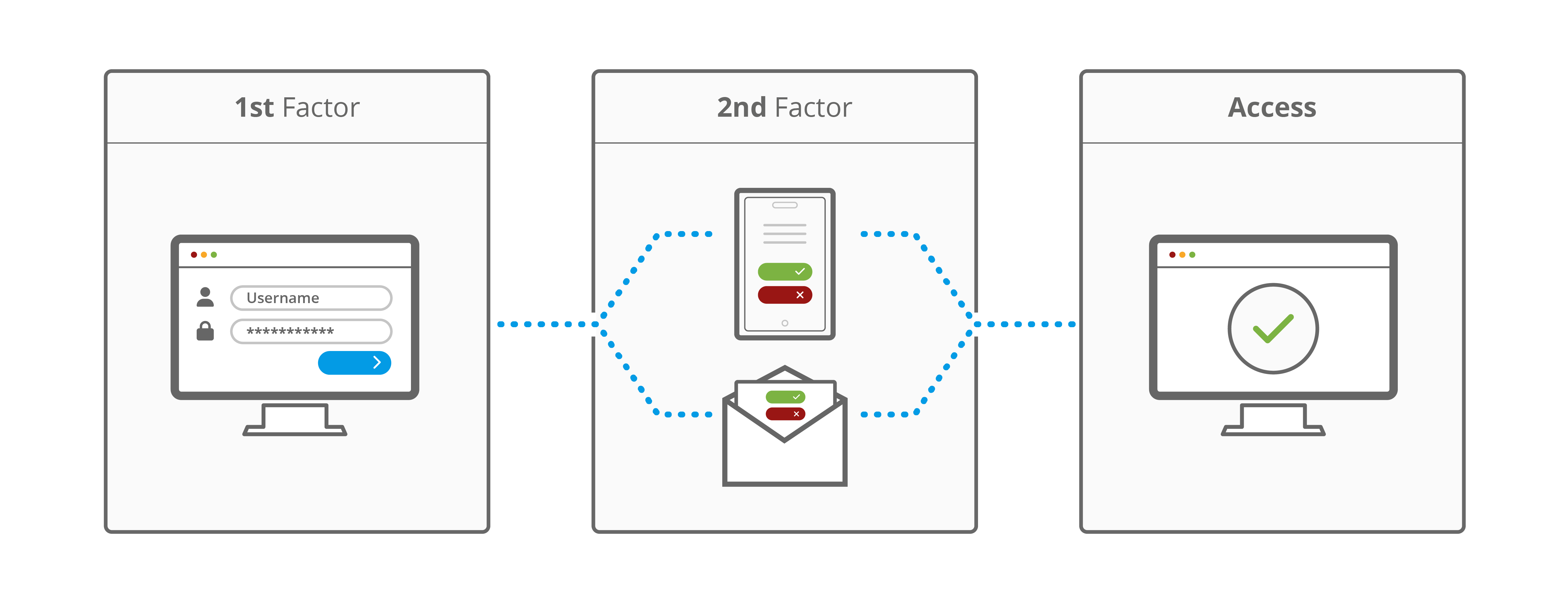
Two-factor Authentication example #
Two-factor authentication can be added to Microsoft accounts by downloading a Microsoft Authenticator app to a mobile. Once registered, every time a log in is attempted to an account on a device, the Microsoft Authenticator app pushes a notification to the device. The notification must then be approved before accessing the requested data.
The app lets you sign in without requiring a password, using your username and your mobile device with your fingerprint, face or PIN.
After you’ve signed in with two-factor authentication, you’ll have access to all your Microsoft products and services, such as Outlook, OneDrive, Office 365, Teams, and more.